Imagine waking up to the news that your company has experienced a data breach. It’s a nightmare scenario, right? Suddenly, you’re dealing with legal ramifications, reputational damage, and the urgent need to understand exactly what happened. In the chaos, having a clear, well-organized data breach documentation template can be an absolute lifesaver. It’s not just about covering your bases; it’s about quickly and efficiently managing a crisis and minimizing the long-term impact.
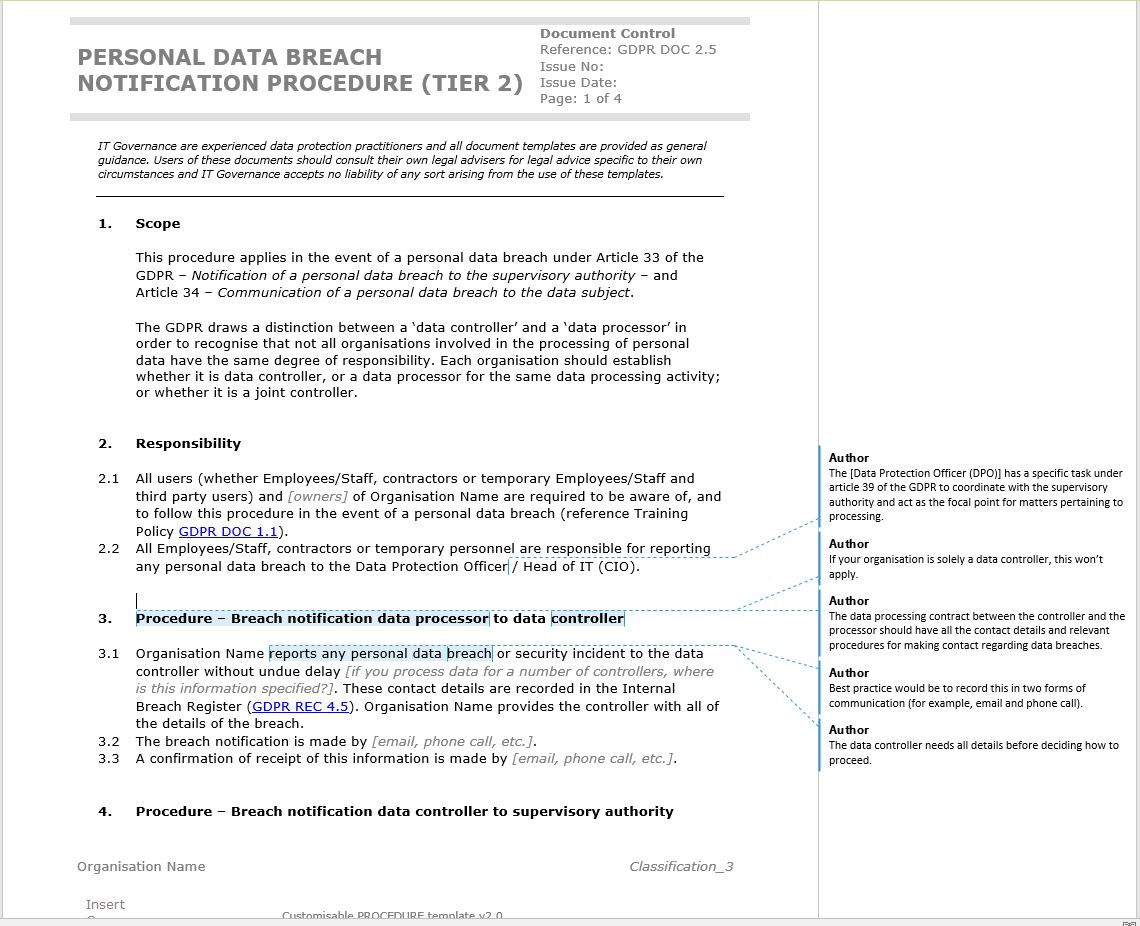
Think of a data breach documentation template as your roadmap through a very complicated and potentially dangerous situation. It provides a structured way to record every step of the incident response process, from initial detection to final resolution. This structured approach is crucial for maintaining accuracy, ensuring compliance with regulations like GDPR and CCPA, and facilitating effective communication with stakeholders, including law enforcement, affected individuals, and the media. Trying to piece things together after the fact is a recipe for errors and omissions, which can significantly worsen the consequences of the breach.
Ultimately, the goal of using a data breach documentation template is to transform a chaotic event into a manageable process. It allows you to systematically gather information, assess the scope of the breach, and take appropriate action. By meticulously documenting each step, you not only demonstrate your commitment to transparency and accountability but also gain valuable insights that can help you prevent future incidents. It’s an investment in your organization’s security posture and its long-term resilience.
Why You Absolutely Need a Comprehensive Data Breach Documentation Template
Let’s face it: data breaches are becoming increasingly common. They’re no longer a question of “if” but “when.” And when that “when” arrives, you need to be prepared. A comprehensive data breach documentation template is the foundation of a strong incident response plan. It’s more than just a checklist; it’s a framework that guides your team through the critical steps of identifying, containing, eradicating, and recovering from a data breach. Without it, you’re essentially navigating blindfolded.
One of the most significant benefits of a data breach documentation template is its ability to streamline the incident response process. During a breach, time is of the essence. A well-designed template ensures that you collect the right information quickly and efficiently, allowing you to make informed decisions and take swift action. This can significantly reduce the impact of the breach and minimize potential damage.
Moreover, a data breach documentation template is essential for compliance. Regulations like GDPR and CCPA require organizations to report data breaches to relevant authorities within a specific timeframe. The template helps you gather the necessary information to meet these reporting requirements accurately and completely. Failing to comply with these regulations can result in hefty fines and reputational damage.
Beyond compliance, a data breach documentation template provides invaluable insights for post-incident analysis. By carefully documenting each step of the response process, you can identify areas for improvement in your security posture and incident response plan. This allows you to learn from your mistakes and strengthen your defenses against future attacks.
Finally, a data breach documentation template fosters transparency and accountability within your organization. It ensures that all stakeholders are aware of the incident and the steps being taken to address it. This can help build trust with customers, employees, and other stakeholders, which is crucial for maintaining a positive reputation in the aftermath of a data breach. In short, it’s about demonstrating that you take security seriously and are committed to protecting the data entrusted to you.
Key Components of an Effective Data Breach Documentation Template
Now that we’ve established the importance of a data breach documentation template, let’s delve into the key components that make it truly effective. A robust template should cover all aspects of the incident response lifecycle, from initial detection to post-incident review. Think of it as a comprehensive guide that ensures no critical step is overlooked.
Firstly, the template should include a section for documenting the initial detection of the breach. This should capture details such as the date and time of detection, the source of the detection (e.g., intrusion detection system, security information and event management (SIEM) system, or employee report), and a brief description of the suspicious activity. This information is crucial for establishing a timeline of events and understanding how the breach was discovered.
Secondly, the template should include a section for documenting the scope of the breach. This involves identifying the systems and data that were affected, the number of individuals whose data was compromised, and the type of data that was exposed (e.g., names, addresses, social security numbers, credit card numbers). This information is essential for assessing the potential impact of the breach and determining the appropriate remediation steps.
Thirdly, the template should include a section for documenting the containment and eradication efforts. This should capture details such as the steps taken to isolate the affected systems, the measures taken to remove the malware or other malicious code, and the actions taken to prevent further unauthorized access. This information is crucial for demonstrating that you have taken steps to mitigate the immediate threat and prevent the breach from spreading.
Fourthly, the template should include a section for documenting the recovery efforts. This involves restoring the affected systems to their pre-breach state, implementing enhanced security measures to prevent future incidents, and notifying affected individuals and regulatory authorities, when applicable. It should also include details on internal and external communication strategies.
Finally, the template should include a section for documenting the post-incident review. This involves analyzing the incident to identify the root cause of the breach, evaluating the effectiveness of the incident response plan, and implementing corrective actions to improve security posture and prevent future incidents. This is a critical step for learning from the incident and strengthening your defenses. Using a robust data breach documentation template is not just about reacting to a crisis; it’s about continuously improving your security posture and building resilience against future attacks.
Having a documented process can make all the difference. When a crisis hits, you want to have the tools ready to make your response smoother and more effective. It is also very important to make sure to keep the data breach documentation template updated.
The implementation of a data breach documentation template is not just about dealing with the inevitable but also about proactive risk management, regulatory compliance, and the long-term resilience of your organization. It represents a commitment to protecting valuable data and maintaining the trust of stakeholders in an increasingly complex digital landscape.