In today’s interconnected world, protecting your assets, whether they are physical property, sensitive data, or intellectual property, is no longer just a good idea—it’s an absolute necessity. Businesses and organizations of all sizes face an ever-evolving landscape of threats, from cyberattacks and data breaches to natural disasters and physical intrusions. Navigating this complexity requires a systematic approach, and that’s where a comprehensive risk assessment and security survey template comes into play.
Imagine having a clear roadmap to identify potential weaknesses, understand the gravity of various risks, and prioritize the most effective security measures. This isn’t just about reacting to problems after they occur; it’s about being proactive, building resilience, and ensuring business continuity. A well-designed template helps you cut through the jargon, organize your thoughts, and gather the crucial information needed to make informed decisions about your security posture. It transforms a daunting task into a manageable process, giving you the clarity you need to safeguard what matters most.
Understanding the Core of Effective Security Planning
At its heart, an effective security strategy begins with a thorough understanding of your current situation and the potential dangers lurking around every corner. This involves two critical components: risk assessment and the security survey. A risk assessment identifies potential threats, analyzes vulnerabilities, and quantifies the potential impact if those threats materialize. It’s about asking “What could go wrong?” and “How bad would it be?” This proactive approach helps organizations move beyond guesswork, enabling them to allocate resources effectively where they are most needed.
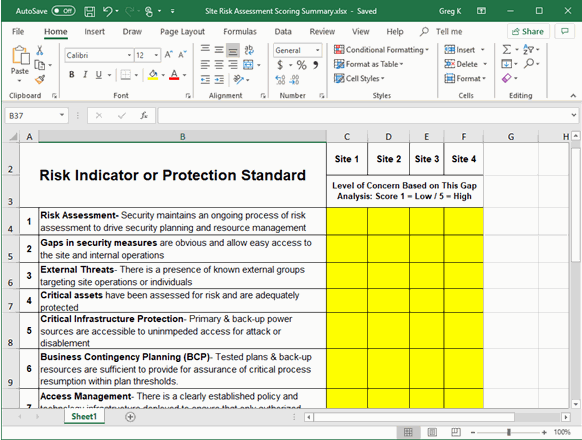
The security survey, on the other hand, is more operational. It’s a systematic review of your existing security controls, policies, procedures, and infrastructure. This hands-on evaluation helps confirm whether your current safeguards are functioning as intended, if there are gaps that need addressing, or if certain areas are over-protected while others are dangerously exposed. Think of it as taking an inventory of your security health, pinpointing specific areas that require immediate attention or improvement to bolster your overall defenses.
When combined, a risk assessment and security survey template provides a powerful tool. It allows you to systematically gather data about your assets, potential threats, current vulnerabilities, and existing security measures. This integrated view ensures that your risk mitigation strategies are directly aligned with your unique threat landscape, rather than generic best practices that might not fully address your specific operational environment. It brings structure and accountability to what can often feel like an overwhelming challenge.
The beauty of using a pre-designed template is that it guides you through this complex process, ensuring no critical stone is left unturned. It provides a consistent framework for evaluation, which is especially valuable for larger organizations or those needing to conduct regular reviews. Without a standardized approach, different individuals might focus on different aspects, leading to inconsistent results and overlooked risks.
Key Elements to Include in Your Template
- Asset Identification: What exactly are you protecting? (e.g., data, physical property, personnel, reputation)
- Threat Identification: What potential dangers could affect your assets? (e.g., cyberattacks, natural disasters, insider threats)
- Vulnerability Analysis: What weaknesses in your current setup could be exploited by threats? (e.g., outdated software, weak physical access controls)
- Existing Controls: What security measures are currently in place to mitigate these vulnerabilities? (e.g., firewalls, access badges, employee training)
- Impact Assessment: If a threat materializes, what would be the financial, operational, and reputational consequences?
- Risk Scoring: A method to quantify and prioritize identified risks (e.g., high, medium, low based on likelihood and impact).
- Recommendations & Action Plan: Specific, actionable steps to mitigate identified risks, assign responsibilities, and set timelines.
Implementing Your Security Posture Enhancements
Once you’ve completed your risk assessment and security survey using a reliable risk assessment and security survey template, the real work begins: implementing the necessary changes. This isn’t a one-time event; it’s an ongoing journey of continuous improvement. Start by reviewing the recommendations generated by your survey. Prioritize them based on the risk scores you’ve assigned. High-impact, high-likelihood risks should be addressed first, followed by those with medium and then low scores. This strategic approach ensures your efforts yield the maximum security benefit with the resources available.
Effective implementation also requires clear communication and collaboration across various departments. Security isn’t just an IT problem; it involves everyone from human resources to operations and legal. For instance, new security policies might require employee training, or physical security upgrades might impact building access. Involving key stakeholders early in the process helps ensure buy-in, facilitates smoother transitions, and increases the likelihood of successful adoption of new measures.
It’s also crucial to define clear responsibilities for each recommended action. Who is accountable for implementing a new firewall? Who is responsible for updating the incident response plan? Without designated owners, tasks can fall through the cracks, leaving critical vulnerabilities unaddressed. Establish timelines and measurable objectives for each action item. This allows you to track progress, celebrate successes, and identify areas where additional support or resources might be needed to keep the implementation on track.
Finally, remember that the security landscape is constantly shifting. New threats emerge, technologies evolve, and business operations change. Therefore, your security posture should also evolve. Schedule regular reviews of your risk assessment and security survey template—at least annually, or more frequently if significant organizational changes occur. This iterative process ensures your security measures remain robust, relevant, and effective against the latest threats, providing enduring protection for your valuable assets.
Taking the time to conduct a thorough evaluation of your current security landscape is a foundational step toward building a truly resilient organization. It moves you from a reactive stance to a proactive one, allowing you to anticipate potential challenges and put measures in place before they escalate into costly incidents. This foresight not only safeguards your tangible assets but also protects your reputation and maintains the trust of your customers and stakeholders.
By systematically identifying vulnerabilities and strategizing appropriate defenses, you create a more secure environment where your business can thrive without constant worry. This disciplined approach fosters a culture of security awareness, ensuring that everyone in your organization plays a role in maintaining a strong defensive perimeter. It’s an investment that pays dividends in peace of mind, operational continuity, and long-term success.